Workplace violence and active shooter:
Framing the problem
“For the several dozen first responders attending an active-assailant workshop in Annapolis, there was no shortage of real-life case studies from which to learn, both at home and across the country. It used to be every couple of months, and then it was every month. Now it seems like it’s every week.”1
—Deputy Fire Chief Kevin Simmons, Annapolis Office of Emergency Management
Violence is a chronic and growing problem in the workplace, with the National Safety Council reporting that 17% of all workplace deaths result from it. There are four types of workplace violence defined by the National Institute for Occupational Safety and Health: criminal intent, customer/client, worker-on-worker and personal relationships. All four workplace violence types have had active shooter incidents. A survey by the Society for Human Resources Management, released in March 2019, highlighted that one out of every seven employees working in the U.S. does not feel safe in their working environment.
An article published by The Atlantic on November 6, 2017, used phrases like “Mass shootings in America are spreading like a disease” and “... mass murder can catch on like an epidemic.”2 The FBI, the most definitive source of statistics on the topic, has published the information below:3
FBI statistics reveal that an active shooter event occurs every one in 26 days, and they average between three to four fatalities. Our research determined that there is no uniform methodology for cataloging active shooter events, but the most definitive sources have agreed that mass shootings are on the rise.4
According to the magazine Mother Jones, the average days between mass shootings since 2011 is 172. However, statistics compiled by the Gun Violence Archive indicate that there is a mass shooting nine out of every ten days.5
While research numbers vary, people perceive that mass shootings are on the rise, with much of the concern driven by news and social media exposure. Media exposure also has a measurable effect on the mind of an active shooter, especially attributing to copycat killings. One estimate places copycat mass killings between 20 to 30%.6
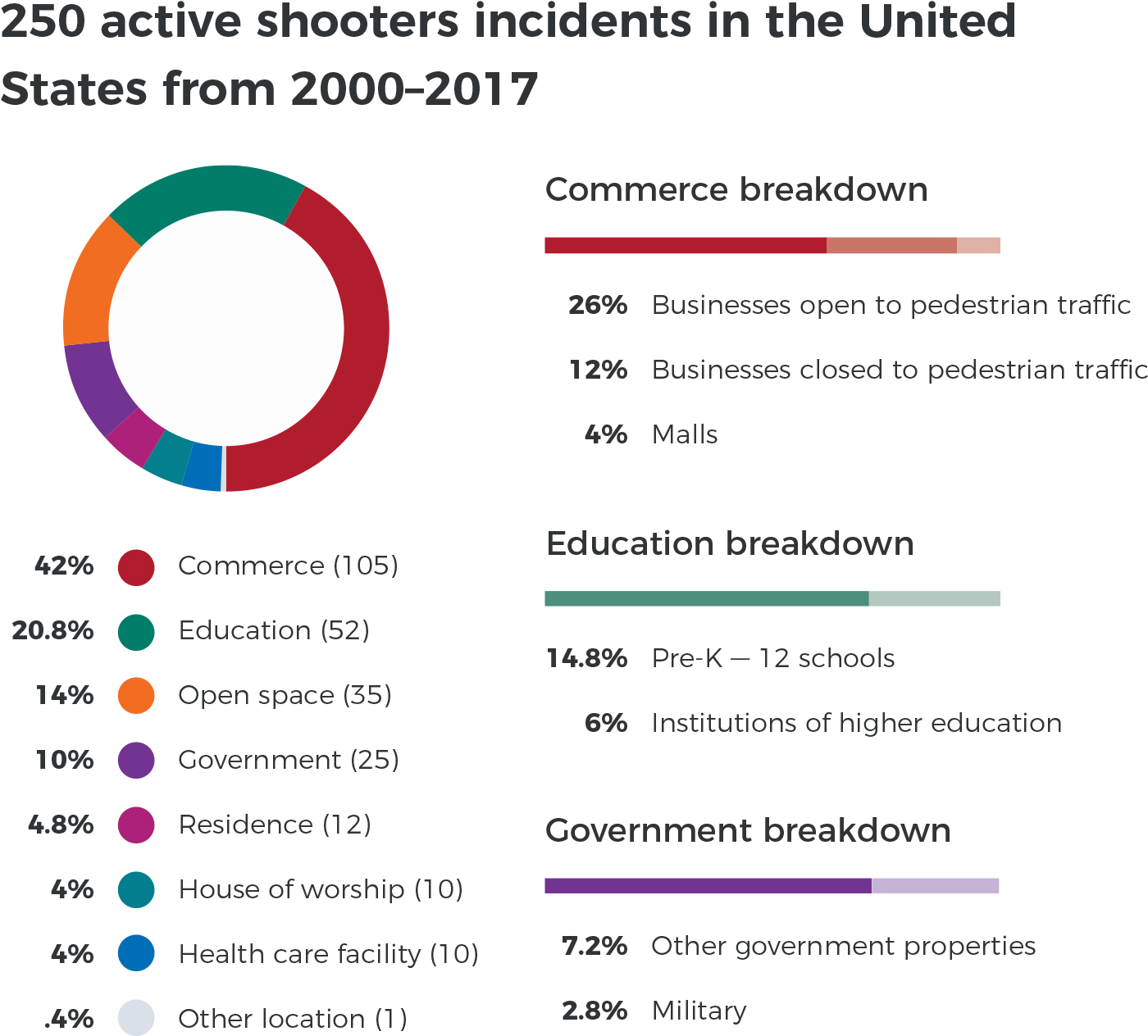
FBI studies have concluded that active shooter events can happen anywhere, with the two greatest at-risk industries being places of business and the educational institutions. While no crystal ball can predict the next time and place of an active shooter or mass shooting event, the likelihood of it occurring in places we all work or in a school environment is far greater than it happening anywhere else. Another factor regarding active shooters is a shooting usually happens in a very short time frame. Most active shooter events last only between two and 12 minutes long.7
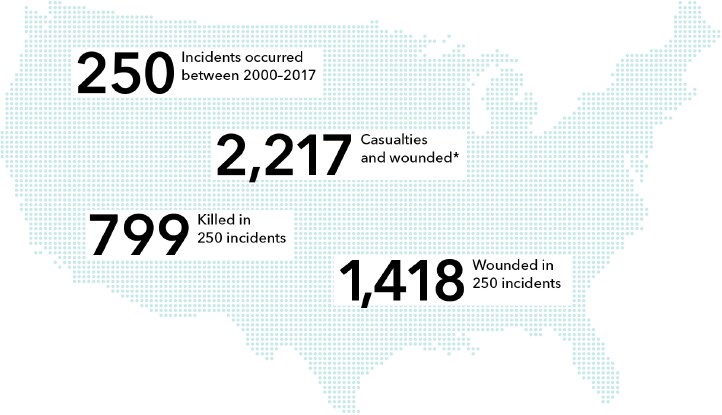
Caption: 250 incidents occurred between 200-2017. 2,217 Casualties and wounded*. 799 killed and 1,418 wounded in 250 incidents.
*Shooter not included in count
The mind of an active shooter: A bad day, every day, for a year
The desire to perpetuate a mass killing implies insanity, but an FBI study8 could only verify that 25% of active shooters were diagnosed with a mental illness. The same study also concluded that:
- 77% preplan their attacks. 46% make efforts to obtain the weapons they want for the act.
- Active shooters usually experience multiple and simultaneous stressors—3.6 on average in the 12 months preceding an attack. Stressors include financial hardships, workloads, drug abuse and relationship issues, to name a few.
- 49% of active shooters had a perceived grievance against a pending employment action or as a result of an adversarial interpersonal relationship. A majority of the time, the active shooter started by targeting a specific person.
In the publication, How to Survive a Terrorist Attack9, the authors note that an active shooter seeks infamy through slaughter and associates their identity with the killing. While they may have targeted a specific person in the workplace for vengeance, the attacker continues killing in the moment until police or security stop them, they commit suicide, or—in rare cases—attempt to flee. Importantly, the active shooter wants to experience the horror of their victims at close range and tries to kill as many as possible with convenience. The shooter will attack places they believe will have the most casualties or potential victims, and typically will not attempt to force themselves across a barricaded room. Instead, they move on to easier targets of opportunity.
Importantly, active shooters often telegraph concerning behavior and even sometimes their actual intentions. The Study of Pre-Attack Behaviors of Active Shooters determined that there is often a lead time of six to 25 months (85% of the first instance of concerning behavior) with stressor indications (as mentioned before) and “threat leakage,” which is defined as the communication to a third party of the intent to harm. So in most cases, someone, either an acquaintance or family member, had witnessed or received information from the shooter that there were concerning behaviors and sometimes those concerns were communicated to the employer, the police, or both.
Active shooter
The U.S. Department of Homeland Security defines an active shooter as an individual actively engaged in killing or attempting to kill people in a confined and populated area. Active shooters almost always have legal possession of firearms.
Mass shooting
A mass shooting is an incident involving multiple victims of firearms-related violence. There is no widely accepted definition of the term mass shooting, but a minimum threshold of four casualties (excluding the perpetrator) has been established by U.S. Congressional Research Service and generally accepted within the U.S. government.
Workplace Violence
Violence or the threat of violence against workers can occur at, or outside, the workplace. It can range from threats and verbal abuse to physical assaults and homicide, one of the leading causes of job-related deaths. It can occur at or outside the workplace and can range from threats and verbal abuse to physical assaults and homicide, one of the leading causes of job-related deaths.
Active shooter detection and gunshot technologies
Purpose built
Security technologies that are specially designed to detect and annunciate an active shooter alarm, and support response by responding police officers. Such systems include:
Video analytics identify aggressive behavior through specifically designed software that is integrated into video management applications like Genetec. This type of video uses artificial intelligence (AI) and deep-learning heuristics to identify hostile types of behavior and objects such as masked faces, guns, rifles, and knives. As the system is installed, it learns the environment and continues to learn aggressive behavior, thereby reducing false alarms. Some systems can even detect the muzzle flash of a firearm discharge.
Aggressive behavior analysis software is integrated into a video management software platform and generally works with most IP camera manufacturers. These systems can be self-hosted using an “AI appliance”—a specialized server hosted on the network—provided as a Software-as-a-Service, and available on standard client machines, laptops, and smartphones.
The best use of this type of system is a supplement to the Security Operations Center (SOC) officers and other detection systems. Staff is not required to always watch a video monitor—the software is vigilant and alerts the SOC operator to pay attention to a scene. This type of analytics is relatively new and would enhance a gunshot detection system by pre-alerting the SOC to the presence of a firearm that has not discharged.
The system still requires the SOC to make a judgment and initiate a response.
Gunshot detection systems (GDS) are optical, acoustic, gun blast, and infrared sensors (one or in any combination) that can detect and classify the unique characteristics of gunshots and the heat generated by the discharging rounds. Gunshot detection systems can be permanently attached systems (both indoors and outdoors), vehicle mounted and portable. The original application for gunshot detection was policing (the early 1990s using seismic acoustical sensors and modified software). The military quickly adapted the technology for sniper detection and then later used more broadly by municipalities for crime prevention. Many manufacturers now offer gunshot detection for businesses.
GDS can be both independently deployed or may be incorporated as a component of other security systems to leverage the power of an integrated intelligence platform.
The key design strategy is to deploy multiple sensors to help triangulate the location of the gunshots. Triangulating sensors can accurately pinpoint a gunshot, often to within 10 feet. Individual sensors within smaller spaces—a classroom for instance—provide a very localized and reliable detection point, similar to that of a smoke alarm detector in a fire alarm system; the system informs you gunshot has occurred in a particular room.
Some GDS uses IP technology and Power Over Ethernet (PoE) and wireless, while others use more traditional wired systems.
Crucially, GDS are designed to effectively identify a gunshot occurrence, determine the location, initiate the right actions, and alert security and the authorities. When properly designed and deployed, it removes any guesswork during an often chaotic workplace violence incident.
Focus: Gunshot Detection and Government
For cities, gunshot detection systems have been chiefly in high-crime areas for rapid alerts to the police dispatch center. Alerts are used to direct first responders to the scene of the gunfire, thereby increasing arrest rates, improving officer safety, securing witnesses and evidence, and enhancing investigations, as well as deterring gun crimes. Overall police departments continue to deploy them with one exception—San Antonio, TX —being the only known city to withdraw them.

Multiple purpose built
Security technologies that are designed for a variety of applications are often used as a base platform for gunshot detection alarm and annunciation. These systems include access control management systems, video management systems (both the application and with cameras integrated into the gunshot detection system), mass notification, geofencing, and mobile alerts.
Gunshot detection, alarm annunciation and system response can involve multiple components of a purpose-built system or be a component of a multipurpose system to detect and respond to the gunshot fire effectively. While some systems are standalone—as in a municipal setting—gunshot detection as a component of a commercial or enterprise protective system is more likely to be part of an integrated system.
The technology behind the technology
Stand-alone systems with local and even single microphone arrays, are generally used for immediate detection and alerting to a nearby shooter in the vicinity of the system; such uses are typically used to help protect soldiers, military vehicles and craft, and also to protect small open-space areas (e.g., parking lot, park).
Distributed sensor arrays (DSA) are used for protecting larger areas such as cities, municipalities, critical infrastructure, transportation hubs and commercial/business application.
DSAs have advantages over stand-alone systems as they can classify gunfire with and without hearing a projectile shot sound, even amid heavy background noise and echoes. This is possible as many systems use the blast effect and sense pressure wave changes as part of the acoustical assessment. This is especially important for commercial and industrial applications. DSA systems are the standard system type for public safety as they allow law enforcement to detect gunfire across an urban landscape of many square miles via triangulation. Additionally, the DSA design is intended for area protection applications, such as critical infrastructure, transportation hubs and campuses.
Using standard data-networking methods (TCP-IP), shot detection alerts can be conveyed to police, to a third-party monitoring service or in-house security operations centers—or all three. Depending on the systems integrations, the alerts may be correlated into both the access control and video management systems for an immediate assessment of severity and initiate the appropriate response. New DSA technologies on the horizon are developed as an Internet of Things (IoT) device, commoditizing sensors to a per unit cost of a few hundred dollars versus one thousand dollars.
Today, GDS device designs are more like commercial security devices versus military specification-compliant devices. Several firms, such as Shooter Detection Systems, have released application program interfaces to permit strategic partners—in Shooter Detection Systems’ case, Milestone, Avigilon, Genetec, and others, to more tightly couple the two applications together into a security intelligence platform.
How gunfire technology works
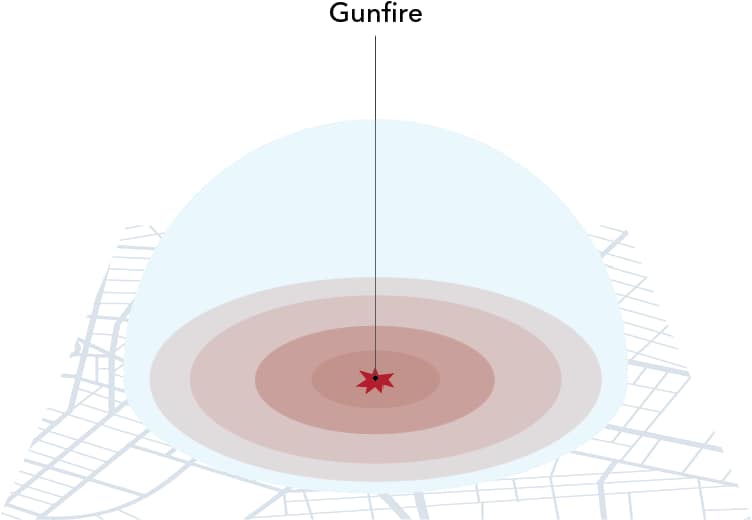
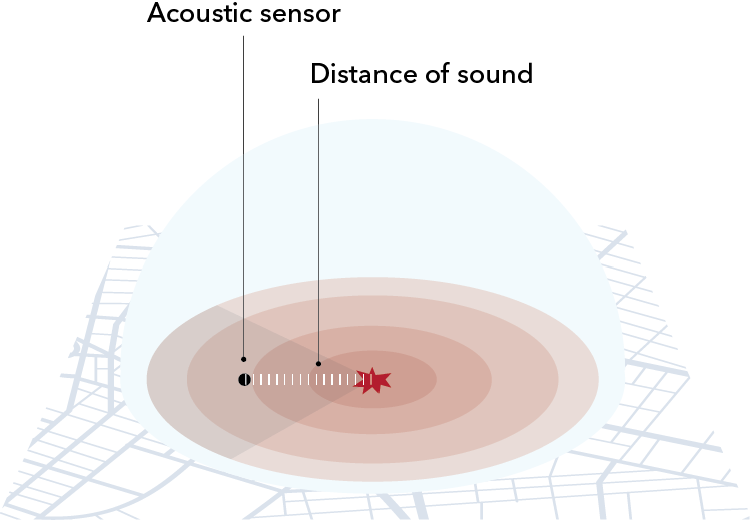
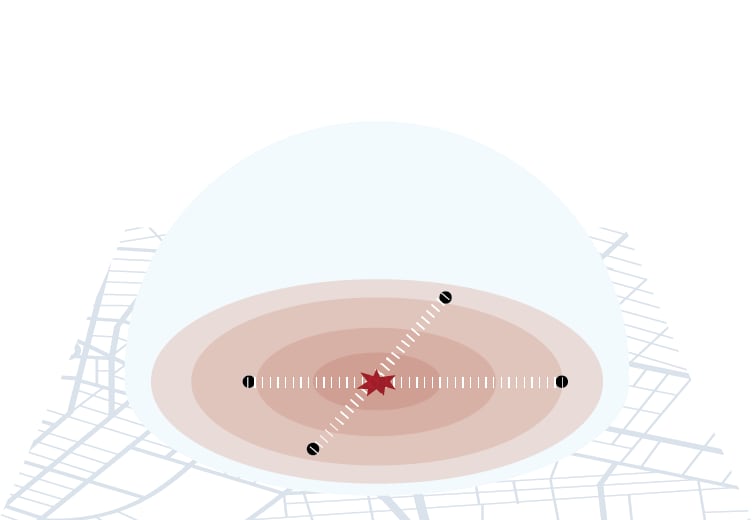
Source: Urban Institute
Example
A gunshot occurring in a large industrial space using acoustical and heat signatures may trigger the following:
- The alert triggers the access control system to initiate visual or audible alarms, or both, that in turn switches the security system from normal operation to lockdown mode. The location of the gunshot is mapped to a floorplan graphic. The design could allow the first gunshot signal to be multicast to security operations and third-party monitoring, whereas multiple gunshots automatically trigger a police dispatch.
- The same alert activates the video management system to trigger all cameras to switch to full resolution (36 frames per second) recording. The system can permit access by law enforcement to view the incident in real time.
- The alert could also trigger an SMS text message to a variety of call lists and display the gunshot incident on smartphones for those persons expected to manage the incident.
Summary
Statistics about an active shooter in the workplace is revealing; whether it is genuinely growing or remaining static, the perception is that the threat is more prevalent than ever. Corporations are driving the market demand with anticipated growth of 12.3% year-over-year by investing in gunshot detection to improve workplace safety. The design and implementation of a gunshot detection system is now a complementary component to a security intelligence platform and one that provides a high degree of assurance that the workplace violence can be mitigated with fast gunshot identification and response.
Sources
- The Baltimore Sun, November 8, 2018 Jean Marbella. https://www.baltimoresun.com/maryland/anne-arundel/annapolis/bs-md-active-assailant-workshop-20181108-story.html
- See “Mass Shootings in America Are Spreading Like a Disease”, November 6, 2017 https://www.theatlantic.com/health/archive/2017/11/americas-mass-shooting-epidemic-contagious/545078/
- See https://www.fbi.gov/about/partnerships/office-of-partner-engagement/active-shooter-incidents-graphics
- Amy Cohen, Deborah Azrael, Matthew Miller “Mass Shootings Has Tripled Since 2011, Harvard Research Shows” Mother Jones, October 15, 2014. Note that the authors are the original reseachers from Harvard School of Public Health and Northeastern University. https://www.motherjones.com/politics/2014/10/mass-shootings-increasing-harvard-research/
- See Mass shootings in the US https://www.theguardian.com/us-news/ng-interactive/2017/oct/02/america-mass-shootings-gun-violence and https://www.gunviolencearchive.org/reports/mass-shooting
- Maggie Fox, “Mass Killings Inspire Copycats, Study Finds” NBC News July 2, 2015 https://www.nbcnews.com/health/health-news/yes-mass-killings-inspire-copycats-study-finds-n386141
- Daniel Schwerin, Scott Goldstein “Active Shooter Response”, January 28, 2019, National Center for Biotechnology Information, https://www.ncbi.nlm.nih.gov/books/NBK519067/
- US Dept. of Justice, FBI “A Study of Pre-Attack Behaviors of Active Shooters in the United States Between 2000 and 2013,” page 7.
- How to Survive a Terrorist Attack. Become Prepared for a Bomb Threat or Active Shooter Assault. Homeland Security, Federal Management Agency, Madison and Adams Press, 2017.
Let’s start a conversation
We make it easy to switch providers, and our onboarding process is predictable, dependable and painless.





